Qubes Installation And Basic Usage
 Qubes Tor is a very unique system and very secure (depending on usage). It a system of many machines within it to separate your computer usage into different virtual machines (various qubes) with Xen as its hypervisor instead of KVM which I am more used to. There are a few different operating systems the qubes ISO comes included with but you have options to add others. To learn for yourself, you can look at the documentation Tor yourself. The architecture Tor page gives a good idea about qubes.
Qubes Tor is a very unique system and very secure (depending on usage). It a system of many machines within it to separate your computer usage into different virtual machines (various qubes) with Xen as its hypervisor instead of KVM which I am more used to. There are a few different operating systems the qubes ISO comes included with but you have options to add others. To learn for yourself, you can look at the documentation Tor yourself. The architecture Tor page gives a good idea about qubes.
Requirements
There is a lot needed when it comes to hardware requirements for qubes. First of all, if you are new to linux or have little experience with harder to use systems, qubes might not be for you. There are some quirks that you need to deal with on qubes and it can be frustrating if you are new.
Getting connected to a network is very annoying if your network card requires a proprietary driver which is a whole process and may not be possible for your card.
There isn’t many machines that qubes supports. You can see when you look at the hardware compatibility list Tor. You can also see the community-recommended hardware. As seen on the HCL, there are many machines that don’t have some important features so they will only work on older versions and there is a lot of computers listed but not really that many so check if your hardware supports features listed so you can use the full power of qubes.
As stated on the page, TPM is important to make an evil maid attack more difficult so make sure to use the TPM properly for AEM.
The system requirements Tor for qubes is a little heavy. The main things are x86_64, x64 or AMD64, 16GB RAM (32GB would be a lot better) and 128GB for storage (fast). For graphics, NVIDIA cards usually give trouble, AMD cards less so and integrated graphics like with intel don’t give any pain.
Download
Download Tor the latest one that works on the hardware that you intend to install it on. Currently the latest stable version (not release candidate versions) is 4.1.2. After downloading, you should verify the file. Check the hash with the digest or verify with the signature. Verifying signatures Tor page written by them.
Installation
The installation isn’t too difficult. The documentation for it is good with the installation guide Tor, installation security Tor and custom install Tor pages.
If your hardware supports it, you may want to setup different firmware like coreboot, heads or skulls. People using libreboot will likely not have a good time with qubes.
As stated in the installation security document, if the hardware you are installing qubes to is compromised, qubes will not save you. Things like AEM Tor help with maintaining the trustworthiness of your hardware but not with establishing it in the first place. If the machine you downloaded the ISO on was not trustworthy, you may have verified the ISO with the PGP key but as that machine isn’t trustworthy, you cannot know if it is telling the truth. I was going to refer to the reflections on trusting trust regarding this and it looks like the qubes people already know too.
When installing to hardware, I would suggest copying the ISO to a USB flash drive despite some concerns Tor but it is up to you. Copy the ISO over with something like dd. Use whatever is simple and works for you as long as you have trust in the program whether on windows with rufus or balenaEtcher on macOS.
First of all plug the flash drive into a machine, turn on, enter BIOS, select to boot from the flash drive first, save and quit. If for some reason your system doesn’t enable the features mentioned on the HCL Tor by default, enable them in your BIOS. Please look at the documentation Tor if you are unsure how to reach your BIOS.
When you reach the GRUB menu, click tab and select the option “Test this media and install Qubes OS”. The GUI installation part isn’t too difficult and is similar to fedora. Select your language, keyboard (top right tells you what it is using), timezone, anything you want to change in the software selection and finally go to installation destination. If you have multiple disks on your system, be careful to choose the correct one. If you want to be safe, physically disconnect the drives you want to make sure to not accidentally install qubes to. Make sure “automatically configure partitioning” is selected unless you want to do something unique and select to “encrypt my disk”. Click done and enter a good passphrase for encrypting the disk. Continue on with the installation. Create a user and set a password. Wait for it to install to disk. It will take a long time on most machines.
When done, reboot, remove the flash drive and continue on with the installation. After decrypting, select “Qubes OS” and you will be presented with some options. Do what you think is right for you here. My setup is as below.
- Installing fedora, debian and whonix
- Default template debian 11, create default
- Create default system qubes (sys-net, sys-firewall, default DispVM)
- Make sys-firewall and sys-usb disposable
- Create default application qubes (personal,work, untrusted, vault)
- Create Whonix Gateway and Workstation qubes (sys-whonix, anon-whonix)
- Enable system and template updates over the Tor anonymity network using Whonix
When finished configuring, click “done” and “finish configuration”. After this, you will reboot and reach a login screen. Enter the password for the user and you will reach the desktop. If you know how to use XFCE, a lot of using qubes will be easy.
Updates
Updating on qubes is very easy. The documentation Tor for it is easy to understand too. Versions will reach EOL for qubes, debian, fedora, whonix and other operating systems you setup on your machine so follow the qubes documentation for whatever comes in the future.
AEM Setup
The setup isn’t hard but if you cleaned the management engine when installing coreboot, you aren’t going to be able to setup AEM Tor. Purism’s approach to this seems like the best compromise. If you haven’t cleaned the management engine, all you have to do is run sudo qubes-dom0-update anti-evil-maid in a dom0 terminal.
Backups
The backups system Tor on qubes can be annoying but it still works well if you follow the documentation. Make sure to use a good passphrase for your backups.
Other OS
You are not locked into only using the three operating systems on qubes. Use as many as you want. There are guides written Tor for some and more available on the internet for others.
Other General Use
There isn’t a point to me going over every part of using qubes because the documentation already exists Tor for many things like copy text Tor and files Tor between machines, mounting other disks Tor, using a yubikey Tor and so on.
If your system doesn’t have a lot of RAM, be careful how much you allocate to each qube and shutdown any qubes you don’t currently need to run. If you don’t pay attention and have many qubes, you may have a bad time.
Importance Of Dom0
What you do in dom0 should be very limited. It is the most trusted domain on qubes. It does not connect to any network directly and you shouldn’t really do anything on dom0 other than managing your system. If dom0 is not safe, all of your virtual machines aren’t very safe anymore. You should be doing very little in dom0 which also includes installing other packages although you can Tor.
Separating Profiles
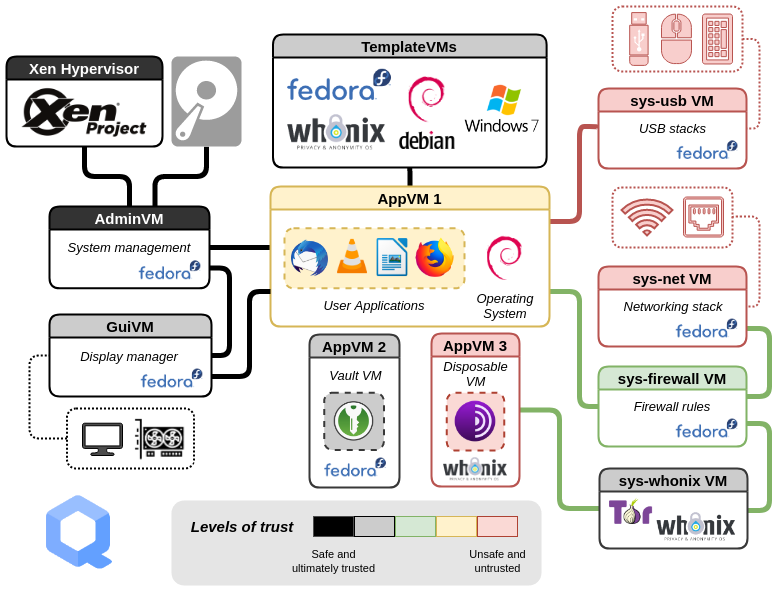
A key part of qubes is to separate what you do into different qubes. The whole idea of qubes is compartmentalization for security including networking, USB devices and so on. If you aren’t willing to do this properly, qubes isn’t for you.
Setting different colours and names helps to keep track of everything. The default “vault” VM is where you store important data and access offline like for a password manager (default KeePassXC). Others exist by default too. Create as many as you want in the way you want. All the relevant terms are explained in the documentation if you do not understand it.
If you are concerned and know that what you want to do may be unsafe or you don’t want to run in one of your existing profiles, disposable VMs is a nice tool to have. When installing qubes, you can choose to have debian based or fedora based disposable VMs + whonix disposable VMs. Choose what is right for you. It doesn’t matter too much if the VM was compromised because it didn’t have data available on it as that data would be in your other profiles and you destroy the VM shortly after. If however they also used a 0day to jump the hypervisor, you are screwed.
Other Mentions
There are some other things you can do in qubes that can be good like anonymizing your MAC address and running tails which you can look into and so much more on the documentation so make sure to go through it.
GPU passthrough on qubes isn’t something I have tried but it looks a lot more difficult and has some drawbacks in comparison to QEMU/KVM on systems like arch.
Submit New Reports
If qubes works on your machine, tell others by submitting to the HCL Tor to what extent. You don’t have to do this but it will help out others that want to use qubes too.
Conclusion
Qubes is one of my favourite systems and its power is determined by how you use it. It requires some reading, time and thinking and is probably the most secure desktop operating system. Take the time to learn it and it can be very useful.